Author: Shiming Zhang (DaoCloud), Wei Huang (Apple), Yibo Zhuang (Apple)
Have you ever wondered how to set up a cluster of thousands of nodes just in seconds, how to simulate real nodes with a low resource footprint, and how to test your Kubernetes controller at scale without spending much on infrastructure?
If you answered "yes" to any of these questions, then you might be interested in KWOK, a toolkit that enables you to create a cluster of thousands of nodes in seconds.
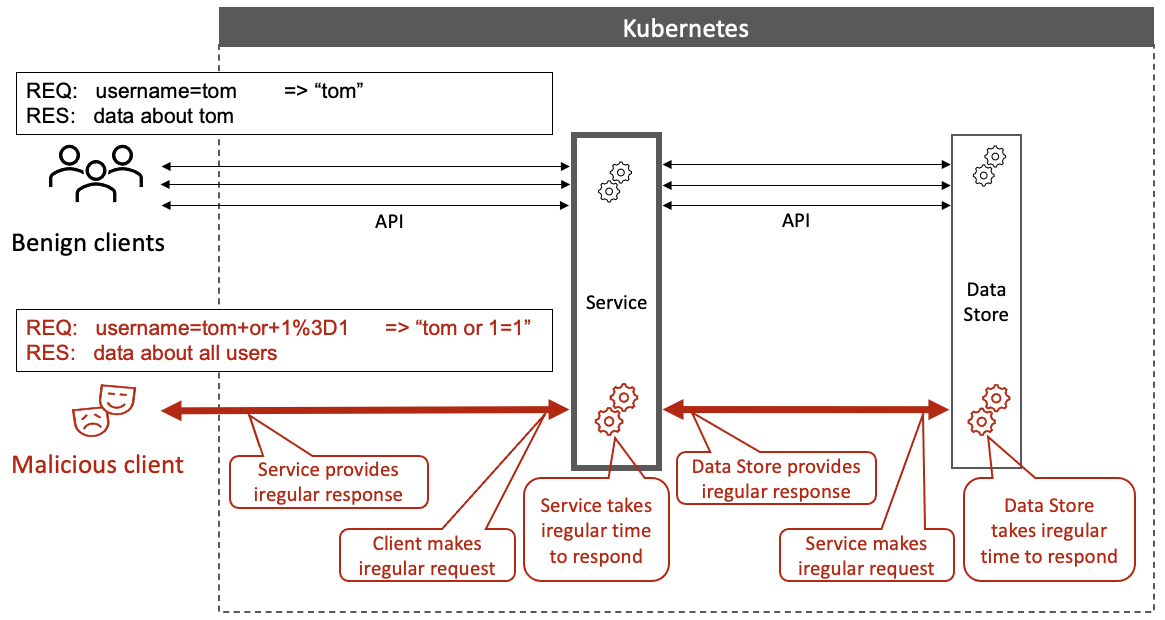 Author: David Hadas (IBM Research Labs) This post
warns Devops from a false sense of security.Following security best
practices when developing and configuring microservices do not
result in non-vulnerable microservices.The post shows that although
all deployed microservices are vulnerable, there is much that can
be done to ensure microservices are not exploited.It explains how
analyzing the behavior of clients and services from a security
standpoint, named here "Security-Behavior
Analysis", can protect the deployed vulnerable
microservices.It points to
Author: David Hadas (IBM Research Labs) This post
warns Devops from a false sense of security.Following security best
practices when developing and configuring microservices do not
result in non-vulnerable microservices.The post shows that although
all deployed microservices are vulnerable, there is much that can
be done to ensure microservices are not exploited.It explains how
analyzing the behavior of clients and services from a security
standpoint, named here "Security-Behavior
Analysis", can protect the deployed vulnerable
microservices.It points to